Steganography, often referred to as the art of hiding, is a fascinating technique that involves concealing information within another medium to ensure secrecy. While cryptography focuses on securing the content through encryption, steganography takes a different approach by hiding the existence of the information itself. This blog post explores the concept of steganography and provides a real-time example to illustrate its practical application.
Understanding Steganography:
Steganography operates on the principle of embedding data within seemingly innocuous carriers, such as images, audio files, or even text. The goal is to make the hidden information imperceptible to the casual observer. Unlike encryption, which may raise suspicions due to the presence of coded messages, steganography hides the very existence of the concealed data.
Real-Time Example:
Hiding a Message in an Image:
Imagine two friends, Alice and Bob, who wish to exchange secret messages without attracting unwanted attention. Alice decides to use steganography to embed a message within an innocent-looking image of a sunset. Let’s walk through the steps of how this process might unfold:
- Selecting an Image:
- Alice chooses a high-resolution image of a sunset as the carrier for her hidden message.
- Creating the Secret Message:
- She composes a short text message that she wants to convey to Bob securely.
- Using Steganography Tool:
- Alice decides to employ a steganography tool, like Steghide, to embed her message into the image.
- Through the command prompt, she executes the command to hide her text message within the image.
steghide embed -cf "sunset.jpg" -ef "secret_message.txt"- Optionally, she can set a password for added security.
- Sending the Image to Bob:
- Once the message is embedded, Alice sends the seemingly innocent image of the sunset to Bob.
- Bob’s Retrieval Process:
- Bob receives the image and knows that there is a hidden message.
- To retrieve the hidden message, he uses the same steganography tool and executes the
steghide extract -sf "received_image.jpg" -xf "output_message.txt"- If Alice set a password, Bob would need to provide it during extraction.
- Decoding the Secret Message:
- After extraction, Bob discovers the hidden text message that Alice intended to convey.
Requirements :
- Image file
- Document that contains your hiding text [document may be anything Eg: txt, doc, pdf, etc.,]
- Windows Operating System
Steps :
Step 1: Place the Image file and the Document in a folder.
Step 2: Zip the document file.
Step 3: Now, Open the Command Prompt and navigate to the folder where you’re having the image and document zip file.
![HIDE TEXT INSIDE IMAGE USING COMMAND PROMPT [STEGANOGRAPHY]](https://bloggerstweet.com/wp-content/uploads/2024/03/stegno1-1024x227.png)
Step 4: Now type copy /b imagefilename + zipfilename output file name [filename with extensions] and hit enter.
Eg: copy /b 1.jpg + 2.zip 3.jpg
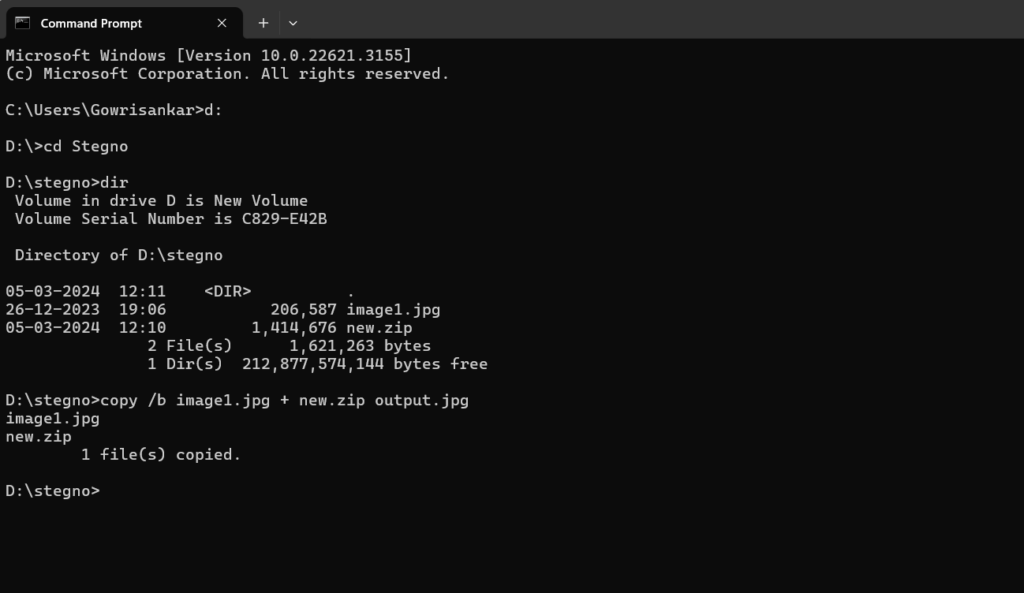
Step 5: Now You can see the size of the image file has been increased.
Step 6: You can now send the image alone to anyone and it contains the document inside it.
How to Extract the document in image :
Step 1: Open the image with unzip tool [We recommend 7Zip]
Step 2: Navigate to the image file location and Click on that image and extract the image.
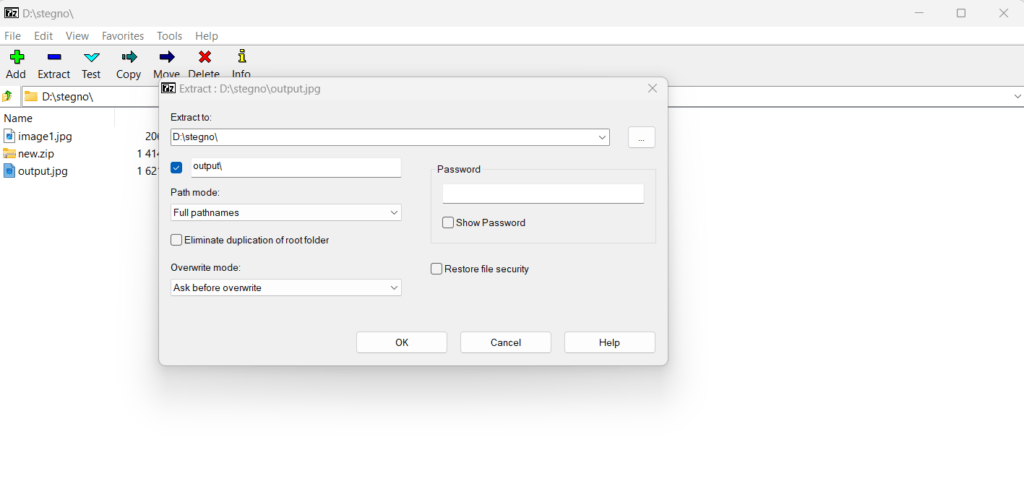
After extraction:

Step 3: You can able to see the document in the extraction.
There are several steganography tools available, each with its own features and capabilities. The choice of the best tool depends on your specific requirements and the type of data you need to hide. Here are some popular steganography tools, along with a brief explanation of each:
Steghide:
- Explanation:
- Steghide is a versatile and widely-used steganography tool. It supports various file formats, including images and audio files.
- It allows users to hide data within the least significant bits of the carrier file, making the changes imperceptible to the human eye or ear.
- Features:
- Password protection for added security.
- Compression of data before embedding.
- Support for different encryption algorithms.
- Usage Example:
- Embedding:
steghide embed -cf image.jpg -ef secret.txt - Extraction:
steghide extract -sf image.jpg -xf output.txt
- Embedding:
OpenStego:
- Explanation:
- OpenStego is an open-source steganography tool that supports multiple carrier formats, including images and audio files.
- It provides a user-friendly interface and offers password protection for securing hidden data.
- Features:
- Easy-to-use graphical interface.
- Password-based encryption.
- Support for various image formats.
- Usage Example:
- Embedding: Load the carrier image, select the data to hide, and set options.
- Extraction: Load the steganographic image, provide the password if applicable, and extract the hidden data.
OutGuess:
- Explanation:
- OutGuess is a steganography tool specifically designed for hiding data in JPEG images.
- It aims to make the changes in the carrier file statistically undetectable.
- Features:
- Specialized for JPEG images.
- Support for multiple passes to enhance security.
- Command-line interface for advanced users.
- Usage Example:
- Embedding:
outguess -d hidden.txt -k passphrase -t cover.jpg stego.jpg - Extraction:
outguess -r -k passphrase stego.jpg extracted.txt
- Embedding:
Steganography Studio:
- Explanation:
- Steganography Studio is a feature-rich steganography tool that supports various carrier formats, including images, audio, and video.
- It provides a user-friendly interface with drag-and-drop functionality.
- Features:
- Support for multiple carrier types.
- Encryption and compression options.
- Intuitive user interface.
- Usage Example:
- Embedding: Load the carrier file, select the data to hide, and configure settings.
- Extraction: Load the steganographic file, provide the necessary credentials, and extract the hidden data.
SilentEye:
- Explanation:
- SilentEye is an open-source steganography tool that supports hiding data in images and audio files.
- It provides a simple interface with basic features for hiding and extracting information.
- Features:
- User-friendly interface.
- Support for various image formats.
- Basic encryption options.
- Usage Example:
- Embedding: Load the carrier image, select the data to hide, and configure settings.
- Extraction: Load the steganographic image, provide the necessary information, and extract the hidden data.
When choosing a steganography tool, consider factors such as the type of data you want to hide, the supported carrier file formats, and the level of security required. Always use such tools responsibly and within legal and ethical boundaries.
Conclusion:
Steganography provides a powerful means of covert communication, allowing individuals to exchange information discreetly. In the digital age, where privacy is a growing concern, understanding steganography is crucial. This real-time example of hiding a message in an image illustrates how this technique can be applied in a practical and secure manner, showcasing the potential of steganography in safeguarding sensitive information. As we delve deeper into the realms of cybersecurity, the role of steganography in ensuring confidentiality continues to grow.


