Introduction:
In today’s interconnected world, the threat of ransomware looms large, posing a significant risk to individuals and organizations alike. Ransomware is a type of malicious software designed to block access to a computer system or files until a sum of money, or ransom, is paid. This blog aims to shed light on what ransomware is, why it’s dangerous, and how you can protect yourself against it. Additionally, we’ll explore some effective prevention tools to fortify your digital defenses.
Understanding Ransomware:
Ransomware operates by encrypting a victim’s files, rendering them inaccessible. Cybercriminals then demand payment, often in cryptocurrency, to provide a decryption key. This type of attack can be devastating, causing data loss, financial harm, and even reputational damage.
Preventive Measures:
Backup Your Data:
Regularly back up your important files to an external hard drive or a secure cloud service. This ensures that even if your data is encrypted, you can restore it without succumbing to the attacker’s demands.
Keep Software Updated:
Cybercriminals often exploit vulnerabilities in outdated software. Regularly update your operating system, antivirus software, and applications to patch security holes and protect against potential threats.
Use Robust Security Software:
Invest in reputable antivirus and anti-malware software. These programs can detect and prevent ransomware attacks before they can cause harm.
Educate Yourself and Your Team:
Awareness is a powerful tool. Train yourself and your team to recognize phishing emails, suspicious links, and attachments. Most ransomware attacks begin with social engineering tactics that trick individuals into unknowingly downloading malicious content.
Limit User Permissions:
Restrict user access rights to the minimum required for their job functions. This minimizes the potential impact of a ransomware attack by limiting the number of files that can be encrypted.
What are the different types of ransomware?
Ransomware comes in various forms, each with its own characteristics and methods of operation. Here are some common types of ransomware:
Encrypting Ransomware:
This is the most prevalent type of ransomware. It encrypts files on the victim’s system, rendering them inaccessible. The user is then presented with a ransom demand in exchange for the decryption key. Examples include CryptoLocker, Locky, and WannaCry.
Locker Ransomware:
Locker ransomware doesn’t encrypt files; instead, it locks the victim out of their entire system, preventing access to files, applications, and sometimes the operating system. The user is typically presented with a full-screen message demanding payment. Examples include WinLocker and Police-themed ransomware.
Master Boot Record (MBR) Ransomware:
MBR ransomware infects the Master Boot Record of a computer’s hard drive, making it impossible to boot into the operating system. Users are then prompted to pay a ransom to restore access. Examples include Petya and Satana.
Mobile Ransomware:
Targeting mobile devices, this type of ransomware affects smartphones and tablets. It may lock the device or encrypt files, demanding payment for restoration. SLocker and Simplocker are examples of mobile ransomware.
Scareware or Fake Antivirus Ransomware:
This type of ransomware displays fake warnings about malware infections, often posing as legitimate antivirus software. Users are coerced into paying for a supposed solution to remove the non-existent threats. Examples include Winwebsec and FakeAV.
Doxware (Leakware):
Unlike traditional ransomware, doxware not only encrypts files but also threatens to publish sensitive data unless a ransom is paid. This adds an element of extortion, as the attackers leverage the fear of data exposure. Notable examples include Maze and REvil (Sodinokibi).
RaaS (Ransomware-as-a-Service):
Ransomware-as-a-Service is a model where cybercriminals rent or purchase ransomware from developers. This lowers the barrier to entry for attackers who may not have the technical expertise to create their own malware. Examples include Cerber and Satan.
Cryptojacking:
While not traditional ransomware, cryptojacking involves secretly using a victim’s computing resources to mine cryptocurrency. Some forms of cryptojacking threaten to increase resource usage or damage hardware unless a ransom is paid.
NotPetya (Petya/ExPetr):
NotPetya is a variant that, while appearing to be ransomware, is often considered a destructive wiper. It encrypts the Master File Table (MFT) and overwrites the Master Boot Record, making data recovery extremely challenging.
Understanding the diversity of ransomware types is crucial for developing effective strategies to prevent, detect, and respond to these threats. Implementing robust cybersecurity practices and using reputable security tools are essential components of a comprehensive defense against ransomware attacks.
Types of Ransomware Attacks
Ransomware attacks can take various forms, and cybercriminals continually evolve their tactics to bypass security measures. Here are some common types of ransomware attacks:
Email Phishing Attacks:
Phishing remains a prevalent method for delivering ransomware. Attackers send deceptive emails containing malicious links or attachments. Once the recipient clicks on the link or opens the attachment, the ransomware is deployed.
Watering Hole Attacks:
In watering hole attacks, cybercriminals compromise websites frequently visited by their target audience. By injecting malicious code into these websites, they infect the computers of visitors, distributing ransomware.
Drive-By Downloads:
Drive-by downloads involve exploiting vulnerabilities in a user’s browser or plugins without their knowledge. Visiting a compromised website can trigger the automatic download and execution of ransomware.
Malvertising:
Malvertising is the use of malicious online advertisements to spread ransomware. Cybercriminals inject malicious code into legitimate ad networks, and users may unknowingly encounter these infected ads while browsing.
Remote Desktop Protocol (RDP) Attacks:
Attackers may exploit weak or compromised RDP credentials to gain unauthorized access to a system. Once inside, they deploy ransomware and demand a ransom for decryption.
Fileless Ransomware:
Fileless ransomware doesn’t rely on traditional executable files. Instead, it operates in the computer’s memory, making detection more challenging. This type often uses scripting languages or exploits legitimate system tools.
Brute Force Attacks:
In a brute force attack, cybercriminals attempt to gain unauthorized access to a system by systematically trying all possible password combinations. Once successful, they may deploy ransomware to encrypt files.
Double Extortion Attacks:
Double extortion involves stealing sensitive data before encrypting it. Cybercriminals threaten to release the stolen information if the victim doesn’t pay the ransom. This tactic increases the pressure on victims to comply.
Ransomware-as-a-Service (RaaS):
RaaS is a model where cybercriminals rent or purchase ransomware from developers. This enables individuals with minimal technical expertise to conduct ransomware attacks, contributing to the proliferation of this threat.
Targeted Attacks (APT):
Advanced Persistent Threats (APTs) involve sophisticated, highly targeted attacks on specific organizations or individuals. Cybercriminals employ advanced techniques to gain persistent access, often deploying ransomware as part of a larger campaign.
Supply Chain Attacks:
Supply chain attacks target vulnerabilities within the interconnected web of suppliers and service providers. By compromising one element of the supply chain, attackers can gain access to multiple organizations, deploying ransomware across the network.
Understanding the variety of ransomware attack vectors is crucial for developing comprehensive cybersecurity strategies. It emphasizes the importance of proactive measures, such as regular security training, vulnerability assessments, and the implementation of robust security protocols, to defend against these evolving threats.
Popular Ransomware Variants
Ransomware is a constantly evolving threat landscape, with new variants emerging regularly. Below are some notable ransomware variants that have gained notoriety due to their impact on individuals, businesses, and organizations:
WannaCry:
Launched in 2017, WannaCry spread rapidly across the globe, infecting hundreds of thousands of computers. It exploited a vulnerability in Microsoft Windows systems, encrypting files and demanding payment in Bitcoin.
CryptoLocker:
One of the earliest ransomware variants, CryptoLocker, emerged in 2013. It used strong encryption algorithms to lock files and demanded payment in cryptocurrency for decryption keys. Though largely dismantled by law enforcement, it paved the way for future ransomware.
NotPetya (ExPetr):
NotPetya, appearing in 2017, was initially thought to be a variant of the Petya ransomware. However, it was later revealed to be a destructive wiper disguised as ransomware. It caused widespread damage by encrypting the Master File Table and overwriting the Master Boot Record.
Locky:
Locky, first detected in 2016, was distributed through malicious email attachments. It utilized strong encryption to lock files and demanded payment for decryption. Locky had multiple variants, contributing to its widespread impact.
Ryuk:
Ryuk is a targeted ransomware that emerged in 2018. It is known for its focus on large organizations and demanding high ransom payments. Ryuk often follows a targeted phishing campaign, compromising networks and encrypting critical files.
Sodinokibi (REvil):
Sodinokibi, also known as REvil, is a Ransomware-as-a-Service (RaaS) that has been responsible for various high-profile attacks. It gained attention for its double extortion tactics, stealing sensitive data before encrypting files.
Maze:
Maze is another ransomware variant known for its double extortion strategy. It not only encrypts files but also threatens to publish stolen data if the ransom is not paid. Maze attacks have targeted organizations in various sectors.
DoppelPaymer:
DoppelPaymer is a ransomware variant that emerged in 2019. It is notable for targeting large enterprises and organizations, often demanding significant ransom amounts. Like other variants, it utilizes advanced encryption techniques.
Conti:
Conti is a relatively new ransomware variant that surfaced in 2020. It is known for its sophistication and is often deployed after initial compromise through other malware. Conti is associated with attacks on healthcare organizations.
DarkTequila:
DarkTequila is a type of ransomware that specifically targets users in Latin America. It spreads through phishing attacks and keylogging techniques, aiming to steal financial information and demand ransom.
It’s important to note that new ransomware variants are continually emerging, and the threat landscape is dynamic. Staying informed about the latest developments, implementing strong cybersecurity practices, and using up-to-date security tools are crucial for defending against ransomware attacks.
How Does Ransomware Affect Businesses?
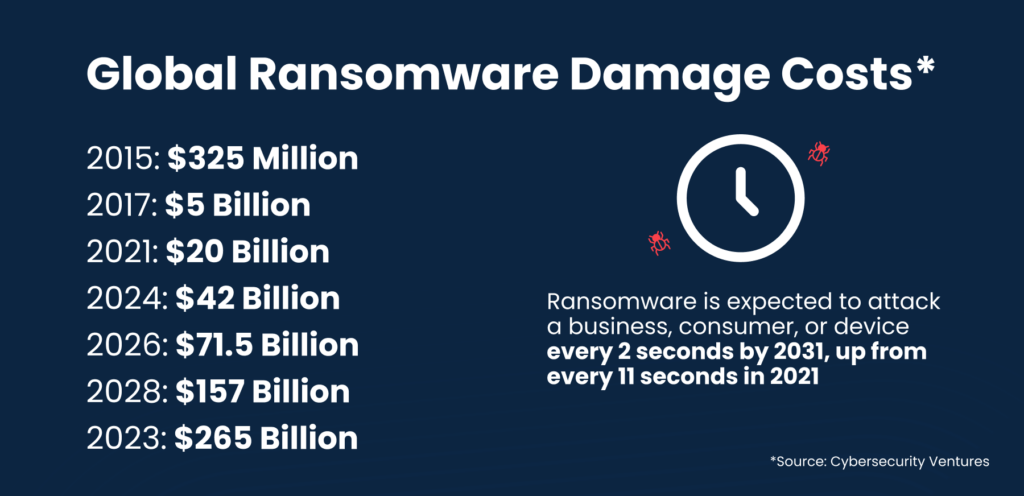
Ransomware can have severe and multifaceted impacts on businesses, affecting operations, finances, and reputation. Here are some ways in which ransomware can impact businesses:
Data Encryption and Loss:
The primary goal of ransomware is to encrypt critical files and data, making them inaccessible to the business. This can lead to significant data loss, affecting operations, customer information, financial records, and intellectual property.
Downtime and Business Disruption:
When essential files and systems are encrypted, businesses may experience prolonged downtime. This disruption can impact productivity, delay projects, and result in financial losses due to the inability to conduct regular business activities.
Financial Losses:
Ransomware attacks often come with a financial demand in exchange for the decryption key. Paying the ransom does not guarantee the retrieval of data, and businesses may still incur financial losses from the ransom payment, potential legal actions, and the costs associated with recovering from the attack.
Recovery Costs:
Recovering from a ransomware attack involves significant costs, including the expense of restoring data from backups, implementing enhanced cybersecurity measures, conducting forensic investigations, and potentially hiring external cybersecurity experts.
Reputation Damage:
Ransomware attacks can damage a business’s reputation, especially if sensitive customer data is compromised. Customers may lose trust in the organization’s ability to secure their information, leading to a decline in customer loyalty and potential legal consequences.
Regulatory Compliance Issues:
Depending on the industry, businesses are often subject to various data protection and privacy regulations. A ransomware attack that results in the exposure or loss of sensitive customer data can lead to regulatory compliance issues, investigations, and fines.
Supply Chain Disruption:
Ransomware attacks targeting one business can have a cascading effect on its supply chain. If the attack disrupts operations or compromises shared systems, it may impact other businesses connected in the supply chain.
Intellectual Property Theft:
Some ransomware variants incorporate data exfiltration, allowing attackers to steal sensitive intellectual property or trade secrets before encrypting files. This poses a long-term threat to a business’s competitive advantage.
Increased Cybersecurity Costs:
In the aftermath of a ransomware attack, businesses are often compelled to invest in more robust cybersecurity measures to prevent future incidents. This can include upgrading security infrastructure, implementing advanced threat detection systems, and providing additional training for employees.
Loss of Customer Trust:
A ransomware incident can erode customer trust, especially if sensitive information is compromised. Customers may choose to take their business elsewhere, impacting revenue and long-term sustainability.
To mitigate the impact of ransomware, businesses should prioritize proactive cybersecurity measures, including regular backups, employee training, robust security protocols, and the use of advanced cybersecurity tools. A comprehensive cybersecurity strategy is essential for protecting against and responding to ransomware threats.
Prevention Tools:
Malwarebytes:
Malwarebytes is a robust anti-malware tool that provides real-time protection against ransomware and other malicious software. Its advanced threat detection capabilities can identify and block threats before they compromise your system.
Windows Defender Antivirus:
For Windows users, Windows Defender Antivirus offers built-in protection against various forms of malware, including ransomware. Ensure it is enabled and regularly updated for optimal security.
Acronis Cyber Protect:
Acronis Cyber Protect integrates backup, anti-malware, and security management into one solution. It provides comprehensive protection against ransomware and facilitates quick data recovery.
Conclusion:
Ransomware is a pervasive threat, but with the right knowledge and tools, you can significantly reduce your risk of falling victim to an attack. By implementing preventive measures and leveraging reliable security tools, you can safeguard your digital assets and maintain peace of mind in an increasingly digital world. Stay vigilant, stay secure!


