In the ever-evolving landscape of web security, one threat that continues to persist is SQL injection. SQL injection occurs when attackers exploit vulnerabilities in your website’s code to execute unauthorized SQL queries, potentially gaining access to sensitive information. In this blog post, we’ll delve into what SQL injection is and explore effective strategies to prevent it from compromising your database.
Understanding SQL Injection:
SQL injection is a type of cyber attack that targets web applications by injecting malicious SQL code into user inputs. These inputs are often forms or other data entry points on a website. When the application doesn’t properly validate or sanitize these inputs, an attacker can manipulate the SQL queries sent to the database, leading to unauthorized access or data manipulation.
What happens if a SQL injection attack is successful?
If a SQL injection attack is successful, private information like the following may be accessed without authorization:
- Passwords.
- credit card information.
- individual user data.
Over the years, numerous high-profile data breaches have made use of SQL injection attacks. Both regulatory sanctions and reputational harm have resulted from this. Sometimes an attacker manages to get a persistent backdoor into the systems of an organization, which can result in a long-term breach that can remain undetected for a long time.
An SQL injection attack happens when:
When data from an unreliable source enters a program, it is not intended.
A dynamic SQL query is created using the data.
The primary ramifications are:
Confidentiality: Since sensitive data is typically stored in SQL databases, SQL Injection vulnerabilities frequently result in a loss of confidentiality.
Authentication: A user without prior knowledge of the password may be able to connect to a system if user names and passwords are not properly checked by SQL commands.
Authorization: If authorization data is stored in a SQL database, then a successful SQL Injection vulnerability attack could be able to alter this data.
Integrity: A SQL Injection attack can allow for the modification or even deletion of sensitive data in addition to the potential for reading it.
How to find vulnerabilities related to SQL injection
By doing a methodical set of tests against each application entry point, you can manually identify SQL injection. Usually, to accomplish this, you would submit:
the lone quotation character “and search for mistakes or other irregularities.”
Certain SQL-specific syntax evaluates to both the entry point’s base (original) value and a new value, and it searches for consistent variations in the application answers.
Boolean conditions like OR 1=1 and OR 1=2, and search for variations in the answers given by the application.
Payloads that, when triggered within a SQL query, are intended to cause time delays and search for variations in response times.
OAST payloads that, when run inside a SQL query, are intended to start an out-of-band network contact and track any that follow.
What are SQL queries
SQL is a standardized language used to access and manipulate databases to build customizable data views for each user. SQL queries are used to execute commands, such as data retrieval, updates, and record removal. Different SQL elements implement these tasks, e.g., queries using the SELECT statement to retrieve data, based on user-provided parameters.
A typical eStore’s SQL database query may look like the following:
SELECT ItemName, ItemDescription FROM Item WHERE ItemNumber = ItemNumber
From this, the web application builds a string query that is sent to the database as a single SQL statement:
sql_query= ” SELECT ItemName, ItemDescription FROM Item WHERE ItemNumber = ” & Request.QueryString(“ItemID”)
A user-provided input http://www.estore.com/items/items.asp?itemid=999 can then generates the following SQL query:
SELECT ItemName, ItemDescription FROM Item WHERE ItemNumber = 999
As you can gather from the syntax, this query provides the name and description for item number 999.
A cheat sheet for SQL Injection: What Is It?
One useful tool for learning about the multiple variations of the SQL injection (SQLi) vulnerability is a SQL injection cheat sheet, which contains extensive technical information. Expert penetration testers can use this SQL injection cheat sheet as a reference, while those who are new to online application security can use it as a general guide.
Getting beyond login screens (SMO+)
Here are several common login techniques that you may employ with form fields and parameters—this is SQL injection 101:
admin' --admin' #admin'/*' or 1=1--' or 1=1#' or 1=1/*') or '1'='1--') or ('1'='1--
Example website:
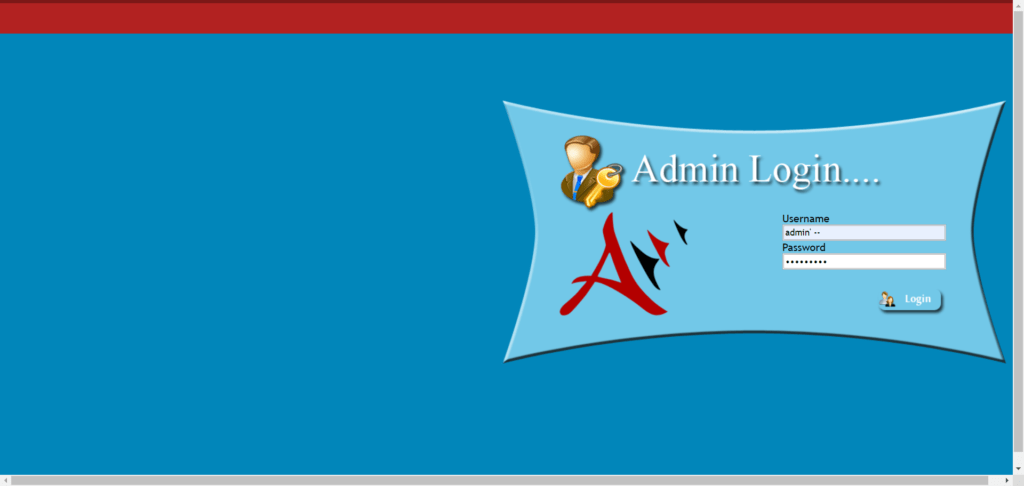
using any query from the cheat sheet:

Preventing SQL Injection:
Use Parameterized Statements: Employ parameterized statements or prepared statements in your SQL queries. Parameterized queries ensure that user inputs are treated as data rather than executable code. This makes it difficult for attackers to inject malicious SQL code.python
Example in Python using SQLite
cursor.execute("SELECT * FROM users WHERE username = ? AND password = ?", (input_username, input_password))
Input Validation and Sanitization: Implement rigorous input validation on both the client and server sides. Validate user inputs against expected formats and reject any inputs that don’t meet the criteria. Additionally, sanitize inputs by removing or encoding special characters that could be exploited in an SQL injection attack.javascript
Example in JavaScript
var sanitizedInput = input.replace(/[^A-Za-z0-9]/g, '');
Least Privilege Principle: Limit the database user’s permissions to the minimum necessary for the application to function. Avoid using accounts with extensive privileges, as this reduces the potential damage an attacker can inflict even if they successfully inject malicious code.
Regular Security Audits: Conduct regular security audits and penetration testing to identify and patch potential vulnerabilities. Regularly reviewing and updating your codebase helps ensure that new security threats are promptly addressed.
Web Application Firewalls (WAF): Implement a Web Application Firewall to filter and monitor HTTP traffic between a web application and the internet. A WAF can detect and prevent SQL injection attacks by analyzing patterns and anomalies in the incoming traffic.
SQL injection prevention for WordPress
Keep WordPress Core, Themes, and Plugins Updated: Ensure that you are running the latest version of WordPress, along with any themes and plugins. Developers frequently release updates that address security vulnerabilities, including those related to SQL injection.
Use Prepared Statements: When interacting with the database in your custom code or plugins, use prepared statements or parameterized queries. This ensures that user inputs are treated as data and not executable SQL code.
Example in WordPress using the global
$wpdb object:php
$wpdb->prepare("SELECT * FROM $wpdb->users WHERE user_login = %s", $username);
Data Validation and Sanitization: WordPress provides functions for data validation and sanitization. Use functions like sanitize_text_field(), intval(), and esc_sql() to sanitize and validate user inputs before using them in database queries.
Example:php
$username = sanitize_text_field($_POST['username']);
Implement Least Privilege: Ensure that your database user has the minimum necessary permissions for the WordPress application to function. Avoid using a database user with overly broad privileges.
Secure Configuration: Review and secure your WordPress configuration files, such as wp-config.php. Remove any unnecessary database information and ensure that your database connection details are kept confidential.
Use Security Plugins: Consider using security plugins that provide additional layers of protection. Plugins like Wordfence or Sucuri Security can help to monitor and block malicious activities, including SQL injection attempts.
Apply Web Application Firewall (WAF): Implement a Web Application Firewall to monitor and filter incoming traffic. A WAF can help detect and block SQL injection attempts before they reach your WordPress application.
Regular Backups: Regularly back up your WordPress site, including the database. In case of a security incident, having a recent backup allows you to restore your site to a secure state.
Security Audits: Conduct periodic security audits to identify vulnerabilities. There are security plugins available that can scan your WordPress installation for potential issues.
Conclusion:
By understanding the risks associated with SQL injection and implementing proactive measures, you can significantly enhance the security of your web application. From utilizing parameterized queries to conducting regular security audits, taking a comprehensive approach to safeguarding your database is crucial in today’s digital landscape. Stay vigilant, stay secure!


